
With the incredible miniaturization of portable SSD storage, you can carry several libraries worth of data in your pocket. But the mix of increased capacity and pocketable form factor creates security risks equally important.
Enter Lokly, a startup building a highly secure USB key that encrypts and decrypts data in real-time as you read or write to it. During CES last week, I met Benoit Berthe, the CEO of Lokly at the French Tech Pavilion, to get a better idea of the security features of its new encrypted USB drive.
There are a number of potential competitors who offer similar functionality on the surface, but Lokly aims to be different in several areas, and the company’s goal for the near future is to get military-grade clearance from ANSSI, the French National Information Security Agency, which is basically the French version of the NSA.

The Lokly USB key in its locked state
When we challenged Lokly with the fact that there are many USB keys that use password or biometrics to AES-encrypt data, Lokly points out that there are security details and real-world usage models that users should pay attention to.
Products that use a strong password often induce a lot of friction because users must remember and type such passwords often (here’s how to generate a strong password, easy to remember), and we know that in practice, many people end up leaving their data unencrypted for that reason, including myself.
“OEMS SOMETIMES HAVE LAX BIOMETRIC SECURITY TO MAKE IT WORK IN THE REAL WORLD (BENOIT BERTHE)”
Lokly’s CEO says that reduce the user experience frictions, manufacturers are often tempted to make the biometric features a little bit laxer (less secure) to account for dirty fingerprints, eyeglasses, new haircut, lousy lighting, and other life realities.
At the end of the day, this means using less biometric data, which is like shortening the length of a password, and that weakens the security to an extent.
Making it easier, without compromising security

The Lokly app uses secure Bluetooth communications to unlock the key after tapping on the Connect button
Lokly wants to solve this by using the phone and an app as the key to the secures USB data. Phone security is well understood, and users are often highly motivated to keep their phones secure for privacy reasons. There can be multiple locks layers (SIM lock, screen lock, app lock) and a hacker would need physical access to the phone and bypass all these layers.

The key is now unlocked

Some folders are mounted on the PC as Read-Only
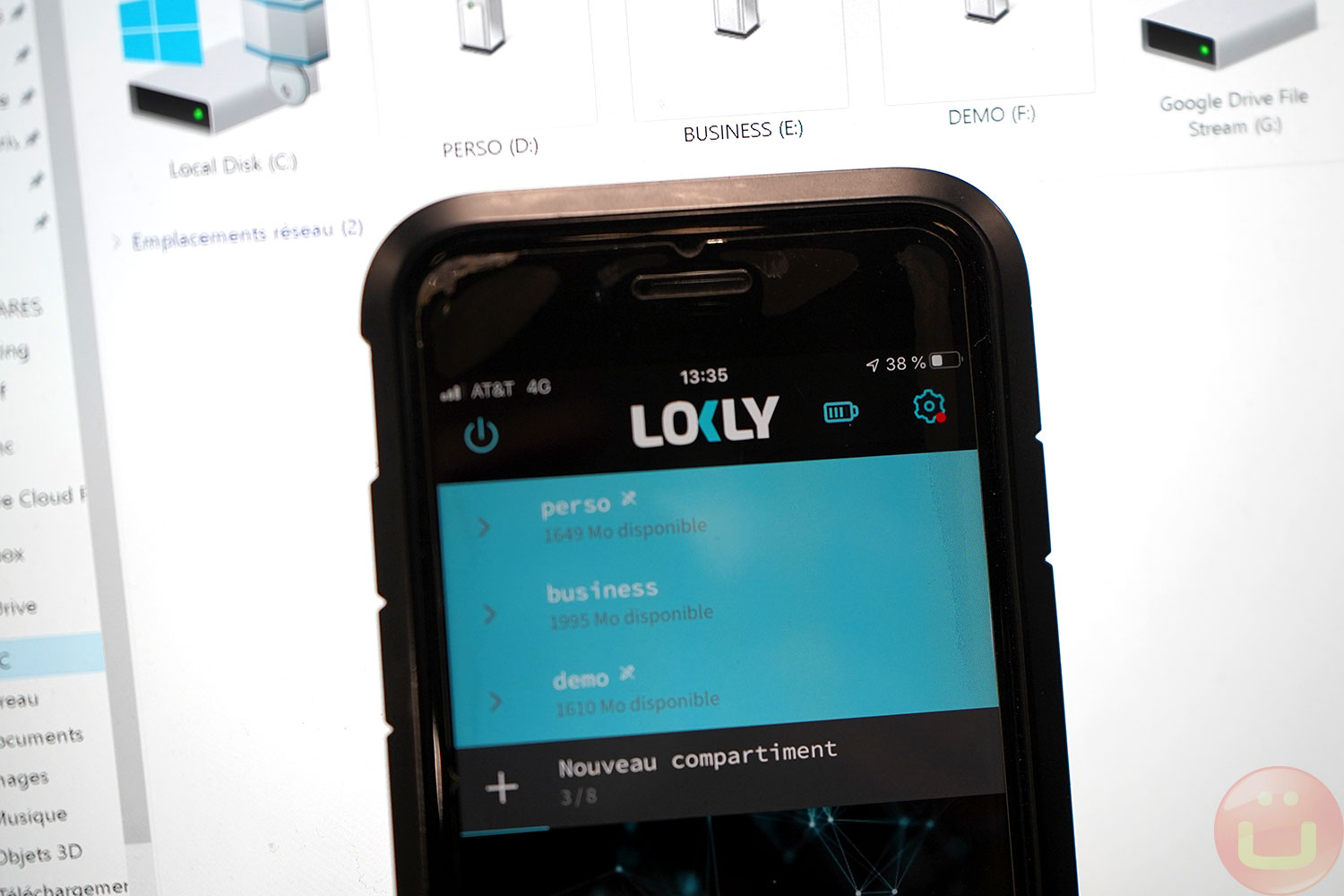
The Lokly app communicates with the USB key over a secure Bluetooth connection. From there, it is possible to mount different directories to the PC (“Personal,” “Business,” and more) and perform basic file management tasks (delete file, etc.).

File-level operations can be done directly via the mobile app, no PC needed
If the phone’s distance to the USB key is too great (~10 yards/meters), the BT connection is severed (Geofencing), and the USB key returns to “locked” mode. This takes care of situations like a lost key or someone snatching it and running away. Of course, the user can also choose to lock the key right from the mobile app when work is done.
Here’s the company’s official presentation video:
Lokly could reduce the hackers’ attack surface
Another thing to be mindful of is that many encrypted USB keys use the host PC processor to encrypt/decrypt data.
This allows such USB keys to reach much higher throughput, but could also enlarge the attack surface for potential hackers, primarily if you use the USB key on a system that you don’t control (public computer, loaner, your client or business partner computer etc.).
An attacker could potentially intercept data by using a hacked storage driver to gain access to information during the data exchange between the secure key and the PC. “You need to have a high degree of confidence in the host PC,” says Benoit Berthe.
“YOU NEED TO HAVE A HIGH DEGREE OF CONFIDENCE IN THE HOST PC”
For that reason, the Lokly key is entirely autonomous and encrypts/decrypts everything using its internal ST Micro hardware platform. It’s true that the peak throughput is lower, but the potential for attack is reduced compared to solutions that require the help of the host PC processor.
In fact, Lokly is so paranoid about the host computer that its USB-key has a female full-size connector to perform key to key copies, without going through a PC.
Lokly says that it has a throughput of 10 MBps (MegaBytes per second) when reading data, and 5 MBps when writing it. That’s the reason why the product has a USB 2.0 connector that can transfer unencrypted data at a maximum rate of 60 MBps.
If you look around, it is common to find PC-size military bulk encryption systems with peak rates of less than 40 MBps (DSD 72A-P, for example).
It’s not evident that such hardware could work within a USB key power envelope, but the point is: with more money and higher production volumes, speed can be improved.
For a startup, pursuing such expensive capital expenditure doesn’t seem like a good idea, but if a large OEM was to license this technology, it would be a whole different game.
If you are less paranoid, consumer-level AES-256 encryption USB keys typically use the powerful host computer’s CPU to handle the encryption. Not only they run at extremely high frequencies (GHz), but they also have a dedicated instruction set to accelerate AES encryption operations. An embedded processor is no match for that kind of power, and these SSDs experience little impact from the encryption workload.
Thwart typical USB hack attacks
Finally, Lokly says it has a mechanism to thwart USB hacks in which a hacker would attempt to place malware onto the key. Because many operating systems execute some actions when a key is plugged to a computer (open the directory, look or preview the files, etc.), there are a high number of possible USB-related hacks.
Lokly says that its key can defend itself against “all hardware attacks,” a bold claim that we cannot vouch for, but worth investigating if you are potentially at risk.
Conclusion
Depending on your security requirements and risk scenarios, Lokly is worth considering. At 240 Euros, it’s not cheap, so if you are “just” afraid to lose your key, perhaps a regular encrypted key might suffice.
“ONLY THE PARANOID SURVIVE (ANDY GROVE, INTEL)”
For business users who don’t want to take any chances with their trade secrets against a potentially sophisticated attack, the extra cost of the key and its relatively low data speed is probably negligible in relation to the possible damages.
It may seem overly cautious, but the Silicon Valley mantra “only the paranoid survive” really applies in many high-stakes situations where the theft of data could have a lasting impact on a company or government.
Lokly Encrypted USB Key For The Most Paranoid Users , original content from Ubergizmo. Read our Copyrights and terms of use.









 Fitbit’s devices from recent years have blood oxygen monitoring (SpO2) hardware, but they haven’t used it — until now. Users on Reddit and elsewhere have noticed that their Versa, Ionic and Charge 3 devices are suddenly (if sometimes temporarily) pr…
Fitbit’s devices from recent years have blood oxygen monitoring (SpO2) hardware, but they haven’t used it — until now. Users on Reddit and elsewhere have noticed that their Versa, Ionic and Charge 3 devices are suddenly (if sometimes temporarily) pr…